In today’s digital age, protecting online privacy has become increasingly crucial. While Virtual Private Networks (VPNs) have been a popular choice for many, they aren’t the only solution. This article explores alternative methods to safeguard your personal information and ensure secure online activities.
Understanding the Limitations of VPNs
While VPNs offer several benefits, they also have their limitations:
- Data Retention: Some VPN providers may log user data, potentially compromising privacy.
- Slow Speeds: VPNs can sometimes slow down internet connections, especially for activities like streaming or gaming.
- Cost: Premium VPN services can be expensive, especially for long-term use.
- Security Risks: If a VPN provider’s servers are compromised, user data could be exposed.
- Jurisdiction: The jurisdiction of a VPN provider can affect the level of privacy protection it offers. For example, VPNs based in countries with strict data retention laws may not provide the same level of privacy as those based in countries with more privacy-friendly laws.
- ISP Tracking: Even with a VPN, your Internet Service Provider (ISP) can still track your online activity based on your IP address.
Alternative Methods to Protect Online Privacy
- Tor Network:

- How it works: Tor uses a network of volunteer-operated relay servers to encrypt and route your internet traffic, making it difficult to track your online activities.
- Benefits: Highly secure, anonymous, and free to use.
- Drawbacks: Can be slow, and some websites may block Tor traffic.
- Additional Considerations: Tor is often used for illegal activities, which can lead to increased scrutiny from law enforcement agencies.
- Secure Browsers:
- Options: Brave, DuckDuckGo, and Tor Browser are popular choices.
- Features: Built-in privacy features like ad-blocking, tracking prevention, and secure connections.
- Benefits: Easy to use, often free, and provide a basic level of privacy.
- Additional Considerations: Some secure browsers may have limitations in terms of compatibility or functionality compared to mainstream browsers.
- DNS Over HTTPS (DoH):
- What is DNS:
- How it works: Encrypts DNS queries, preventing ISPs and other third parties from monitoring your browsing history.
- Benefits: Improves privacy and can enhance website loading speeds.
- Drawbacks: May not be supported by all devices or internet service providers.
- Additional Considerations: Some DoH implementations may have security vulnerabilities, so it’s important to choose a reputable provider.
- Self-Hosted DNS:
- How it works: Setting up your own DNS server provides complete control over your DNS queries.
- Benefits: Maximum privacy and control, but requires technical expertise.
- Drawbacks: Can be complex to set up and maintain.
- Additional Considerations: Self-hosted DNS can be time-consuming and may require specialized hardware or software.
- HTTPS Everywhere:
- How it works: Automatically redirects HTTP traffic to HTTPS, ensuring secure connections to websites.
- Benefits: Simple to install and use, provides a basic level of privacy.
- Drawbacks: May not work with all websites, especially those with outdated security certificates.
- Additional Considerations: While HTTPS Everywhere can improve privacy, it’s not a complete solution and should be used in combination with other security measures.
- Ad-Blockers:
- How it works: Block advertisements and trackers that collect user data.
- Benefits: Improves privacy, reduces distractions, and can improve website loading times.
- Drawbacks: Some websites may rely on ad revenue and could be affected.
- Additional Considerations: Some ad-blockers may have limitations or may not block all types of tracking.
- Private Search Engines:
- Options: DuckDuckGo, Startpage, and Searx are popular choices.
- Features: Do not track user search queries or personalize results.
- Benefits: Protects privacy and provides unbiased search results.
- Additional Considerations: Private search engines may not have the same level of indexing or search results as mainstream search engines.
- Two-Factor Authentication (2FA):
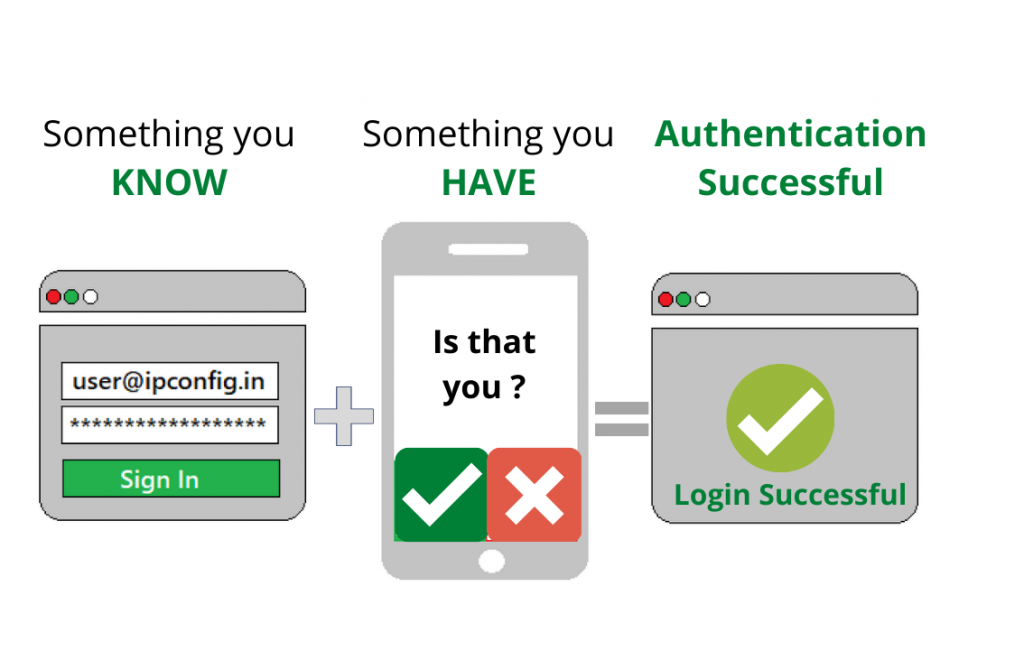
- What is 2 Factor Authentication (2FA) and why it is Important ?
- How it works: Requires a second form of verification, such as a code sent to your phone or a security token.
- Benefits: Significantly enhances account security, making it more difficult for unauthorized users to access your accounts.
- Drawbacks: Can be inconvenient, especially if you lose your phone or security token.
- Additional Considerations: Two-factor authentication should be enabled for all important online accounts, such as email, social media, and banking.
- Secure Messaging Apps:
- Options: Signal, WhatsApp, and Telegram are popular choices.
- Features: End-to-end encryption, ensuring that only you and the recipient can read your messages.
- Drawbacks: Some messaging apps may have limitations in terms of features or compatibility.
- Additional Considerations: It’s important to choose a messaging app that has a strong reputation for security and privacy.
- Regular Software Updates:
- Why it’s important: Updates often include security patches that address vulnerabilities.
- How to stay updated: Enable automatic updates for your operating system, browser, and other software.
- Drawbacks: Updates can sometimes introduce new bugs or glitches.
- Additional Considerations: It’s important to be aware of the potential risks and benefits of software updates and to weigh them carefully before deciding whether to install them.
Beyond the Basics
In addition to the methods mentioned above, there are several other strategies you can employ to protect your online privacy:
- Be cautious about sharing personal information online. Avoid sharing sensitive information like your full name, address, phone number, or social security number on public forums or social media.
- Use strong, unique passwords for all of your online accounts. Avoid using the same password for multiple accounts, and consider using a password manager to help you create and manage strong passwords.
- Be aware of phishing scams. Phishing attacks are often designed to trick people into revealing their personal information. Be cautious of emails, text messages, or phone calls that ask for sensitive information.
- Use a firewall. A firewall can help protect your computer from unauthorized access.
- Consider using a hardware security key. A hardware security key can provide an additional layer of security for your online accounts.
- Stay informed about the latest security threats and best practices. Keep up-to-date on the latest security news and trends to ensure that you are taking the necessary steps to protect your privacy.
Additional Considerations
- Privacy-Focused Operating Systems: Consider using privacy-focused operating systems like Tails or Linux distributions with built-in privacy features.
- Tor Browser Bundles: Use Tor Browser bundles that include additional privacy tools like ad-blockers and tracking protection.
- Offline Activities: Remember that not all online activities can be completely protected. Consider engaging in offline activities to reduce your digital footprint.
- Legal Considerations: Be aware of the legal implications of using certain privacy tools or techniques, especially in countries with restrictive internet laws.
- Personal Risk Assessment: Evaluate your personal risk factors and adjust your privacy measures accordingly. Consider factors such as the sensitivity of your personal information, your online activities, and the potential consequences of a privacy breach.
Conclusion
While VPNs can be a valuable tool for online privacy, they are not the only solution. By combining multiple methods, such as secure browsers, DNS encryption, and two-factor authentication, you can create a more robust and comprehensive privacy shield. Remember, online privacy is an ongoing process, and it’s essential to stay informed about emerging threats and best practices.





